What is the MITRE ATT&CK Framework?
The MITRE ATTACK Framework is a curated knowledge base that tracks cyber adversary tactics and techniques used by threat actors across the entire attack lifecycle. The framework is meant to be more than a collection of data: it is intended to be used as a tool to strengthen an organization’s security posture.
For instance, because MITRE ATT&CK takes the perspective of the adversary, security operations teams can more easily deduce an adversary’s motivation for individual actions and understand how those actions relate to specific classes of defenses.
Where does the data in the MITRE ATTACK Framework come from?
MITRE’s ATT&CK is populated mainly by publicly available threat intelligence and incident reporting, as well as by research on new techniques contributed by cyber security analysts and threat hunters. It is used by those same professionals to better understand the different ways bad actors might operate so adversarial behavior can be detected and stopped.

CrowdCast:MITRE Engenuity ATT&CK Evaluations: Inside the Enterprise Round 5 Results
Get an inside look into 2023’s MITRE ATT&CK Round 5 evaluation and learn how CrowdStrike delivered 100% in protection, visibility and detection.
Tune In
History of MITRE ATTACK Framework
MITRE is a nonprofit organization created to provide engineering and technical guidance to the federal government. The organization originally developed the framework for use in a MITRE research project in 2013 and named for the data it collects, which is Adversarial Tactics, Techniques, and Common Knowledge-or, in acronym form, ATT&CK.
MITRE ATT&CK was released to the public for free in 2015, and today helps security teams in all sectors secure their organizations against known and emerging threats. And while MITRE ATT&CK originally focused on threats against Windows enterprise systems, today it also covers Linux, mobile, macOS, and ICS.
Here are three iterations of MITRE ATT&CK:
- ATT&CK for Enterprise: Focuses on identifying and imitating adversarial behavior in Windows, Mac, Linux, and cloud environments.
- ATT&CK for Mobile: Focuses on identifying and imitating adversarial behavior in Android and iOS operating systems.
- ATT&CK for ICS: Focuses on describing the actions adversaries might take when they operate in an industrial control system (ICS).
Expert Tip
The MITRE ATT&CK™ framework is an ambitious initiative that is working to bring clarity to how we talk about cyberattacks. Learn how CrowdStrike demystifies threats with the MITRE ATT&CK framework.Read Blog
The MITRE ATT&CK Matrix: tactics and techniques
Specific adversaries tend to use specific techniques. The MITRE ATT&CK Framework catalogs information that correlates adversary groups to campaigns, so security teams can better understand the adversaries they are dealing with, evaluate their defenses, and strengthen security where it matters most.
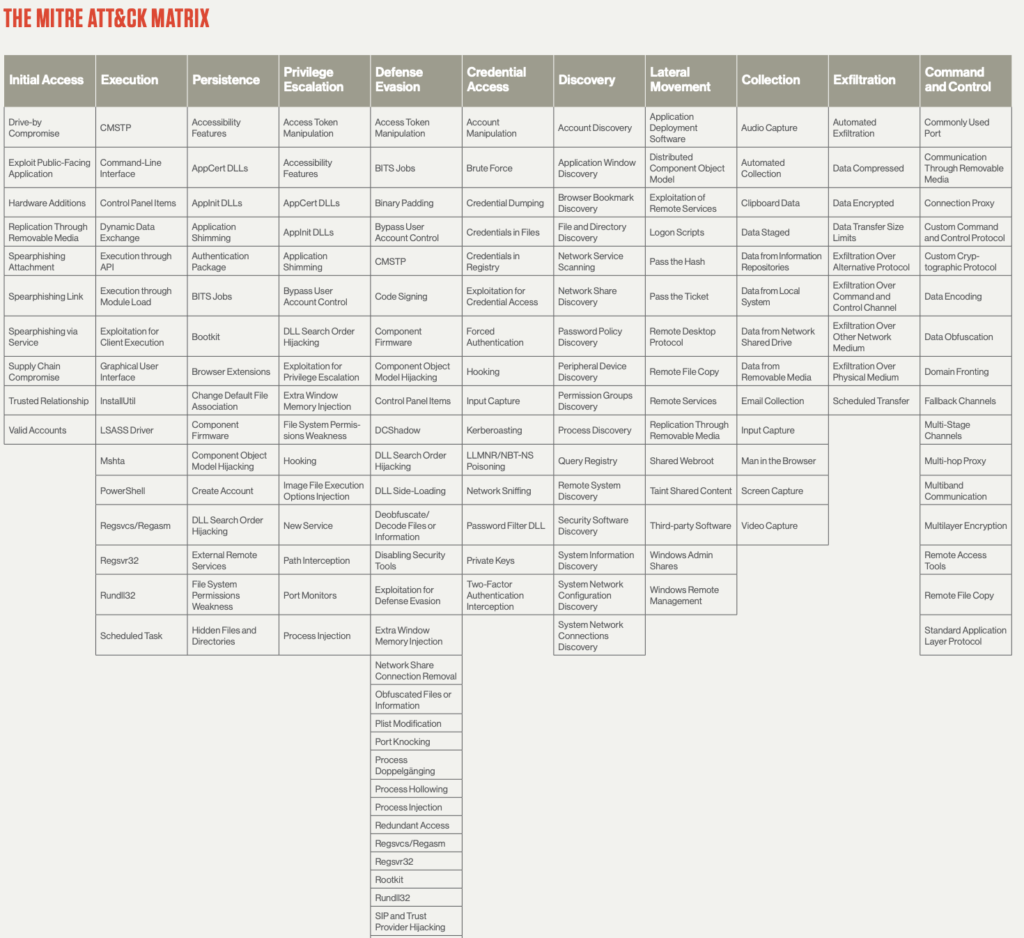
What are MITRE ATT&CK tactics?
Adversarial tactics are specific technical objectives that an adversary intends to achieve.Tactics are categorized according to these objectives. For instance, there are currently 14 tactics cataloged in the enterprise matrix:
- Reconnaissance: Techniques that actively or passively gather information to plan future targeted attacks.
- Resource development: Involves attackers purchasing or stealing resources to use them for a future attack.
- Initial access: Techniques where adversaries try to gain a foothold in your network through different attack vectors.
- Execution: Adversary techniques that try to run malicious code on a local or remote system.
- Persistence: Tactics that involve adversaries trying to maintain their foothold in your local or remote network.
- Privilege escalation: When an adversary tries to gain higher-level permission into your organization’s network.
- Defense evasion: Adversary techniques to avoid detection when they move through your network.
- Credential access: Tactics focused on retrieving sensitive credentials such as passwords.
- Discovery: When adversaries try to gain an understanding of how your systems work.
- Lateral movement: Involves adversaries that enter and control systems, moving through your network.
- Collection: Techniques that gather information from relevant sources within your organization.
- Command and Control (): When adversaries communicate with compromised systems to gain control.
- Exfiltration: Consists of techniques that straight up steal data from your network.
- Impact: When adversaries focus on disrupting data availability or integrity and interrupting business operations.
What are techniques?
A technique describes one specific way an adversary may try to achieve an objective. A multitude of techniques are documented under each “tactics” category. This is because adversaries may use different techniques depending on factors such as their skills sets, targets’ system configuration aned availability of suitable tools.
Each technique includes a description of the method, the systems and platforms it pertains to, which adversary groups use it (if that is known), ways to mitigate the activity, and references to its use in the real world.
MITRE ATT&CK currently identifies 188 techniques and 379 sub-techniques for enterprise.
What are procedures?
Procedures are the step-by-step descriptions of how an adversary plans to achieve their objective.
MITRE ATT&CK vs. Cyber Kill Chain
Another popular cybersecurity framework used in threat detection and threat hunting is the Cyber Kill Chain. Unlike MITRE ATT&CK, which is a matrix of techniques, the Cyber Kill Chain defines a sequence of events. Developed by Lockheed Martin, the Cyber Kill Chain is modeled on the military concept of a kill chain, which describes the structure of an attack.
There are seven steps in the Cyber Kill Chain:
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command & Control (C2)
- Actions on Objectives
Although the Cyber Kill Chain, along with another security framework called the Diamond Model are still in use, the MITRE ATT&CK Framework is the most widely adopted today. Unlike the older frameworks, MITRE ATT&CK indexes everything about an attack from both the attacker and defender sides. Attack scenarios mapped by MITRE ATT&CK can be replicated by red teams and tested by blue teams.
What are some use cases of the MITRE ATT&CK Matrix?
Some of the ways a security team can use MITRE ATT&CK include:
- Conduct a security gap analysis and plan security improvements
- Strengthen cyber threat intelligence
- Accelerate Alert Triaging and Investigation
- Create more realistic scenarios for red team exercises and adversary emulations
- Assess maturity of security maturity of their SOC
- Communicate clearly and concisely to stakeholders
- Acquire a common language which is helpful when working with consultants and vendors
Learn More
Read our blog post on how CrowdStrike’s Elite Managed Services operate in the real world.